Using a Secure Anonymous Proxy Online
Proxies, free ones, secure ones, anonymous ones – so why is everyone obsessed with them? Various reasons – but the truth behind proxies anonymous is that people are fed up with being controlled, logged, censored and blocked on the internet. If you start searching on the internet for terms like privacy and anonymity it won’t be long before you stumble across the concept of using proxies, and with very good reason.
But I have a problem with anonymous proxies, and it’s a big problem, it’s one of security and how some people who use these servers are being exploited. I am of course referring to the dreaded anonymous free proxies which people use without any perception of the risk they are taking.
What is an Anonymous Proxy?
So, before I get on my soap box, there’s some things I should address – the very first thing should be what is an anonymous proxy, and what is it actually used for?
It’s a good question – I’ve worked in IT for about 20 years now and lots of my colleagues wouldn’t really have much of a clue, the rather basic assumption is that if you send your data through proxies anonymous, you’ll be secure is at best incorrect and at worse completely wrong.
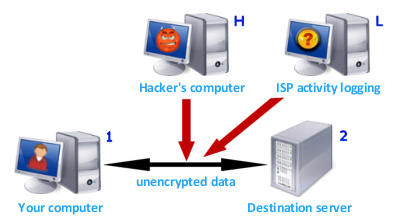 Direct HTTP Surfing (No Proxy)
Direct HTTP Surfing (No Proxy)
So here we are, this illustration shows how vulnerable our normal browsing is, the biggest danger this diagram illustrates is the fact that the vast majority of our browsing over the internet is in clear text. So, for instance all your browsing will be directed through the ISP where it is logged, this contains the most complete record of everything you do online. The simple reason that European and US Directives are forcing ISPs to store these logs is that it is the easiest place for them to get a complete record of what each individual does on the internet.
HTTP is Not a Secure Protocol
The main problem in this case is HTTP (Hyper Text Transport Protocol), it’s a fast and efficient way of communicating and delivering content across the internet. Unfortunately, it has no concept of security or privacy, it’s all readable and in clear text. The same goes for the ISP logs, they all contain a huge readable list of everything you do online, web sites, videos, pictures and downloads. If someone is snooping or sharing your wifi connection, they can read it all too.
The funny thing is an anonymous proxy doesn’t help at all in this instance. You could surf via the highest security, super anonymous proxy server in the world and you’d still leave a complete list of everything you do online in ISP logs and lots of other routers and switches.
This really does mean everything too; all activity is logged automatically. So even if you just download your email, watch the BBC News online and check your stocks and share prices that’s all registered. It’s easy to see why this information is so valuable as it builds up a comprehensive profile of whoever you check out.
Encrypt your Logs !
There is only one way to protect against these logs and that is to encrypt your connection. The simplest way to do this is to create an encrypted tunnel and surf through this. Some sample methods are using SSH or SSL tunnels, or directly through a VPN (Virtual Private Network). In all these situations then your internet activity is still logged but it is unreadable and encrypted.
The Proxies Anonymous Problem
So why does anyone bother with an anonymous proxy, well the answer is simple, proxies help in one particular situation. That is – they stop your IP address being logged in the web site you visit. Encryption won’t help this because your IP address is not protected, although the data being transferred is protected. A proxy server is a machine that sits between you and the web sites you visit and transfers all requests without revealing your IP address. At least as long as it is configured correctly, the only address that will be revealed is the IP address of the anonymous proxy server itself.
So, the two fundamental security issues on the internet can be solved by encryption and a secure anonymous proxy. Here’s how your connection looks when you use Identity Cloaker – it creates an encrypted tunnel to forward all web requests and then allows you to surf through a huge network of fast private proxies.
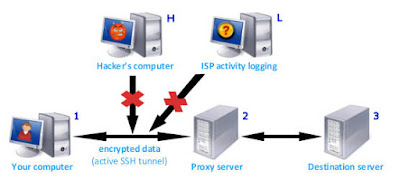 Safe Browsing – Encrypted and Proxied
Safe Browsing – Encrypted and Proxied
VPNs and Proxies Give Privacy
It’s the most secure way of browsing the internet available today. It’s also fast and private, for the most part you won’t notice any difference in speed.
Most importantly it bypasses one of the biggest security mistakes people make online – the use of free anonymous proxies. Unfortunately, privacy costs, proxy servers are extremely expensive to run mainly due to the bandwidth charges. This is why is surprising to see the number of free anonymous proxies available.
Well, I can explain this as apart from the simple web proxies which allow to type in a url directly, the true proxies available for free are either.
-
- Servers which have misconfigured and accidentally left open
-
- Hacked servers which are used to harvest usernames and passwords by identity thieves
Proxies with Permission
In both respects they are extremely insecure, although obviously the ones run by identity thieves are the most worrying. These are not little hacker or script kiddies either, they are extensive criminal gangs with the infrastructure to exploit accounts, passwords and credit card details quickly and ruthlessly.
You can with technical knowledge and access to resources produce a secure environment for your surfing, but it should never involve using a free anonymous proxy. If you do then you are potentially sending everything you do via a gang of Identity Thieves, which is about as clever as sending your bank account details to help a Prince in Nigeria who needs help! (If you don’t follow that – Google ‘419 scams’)
You can get a decent secure proxy here (which also works well with the BBC)