Introduction to SSL
We’ve all ordered products online, and seen the little lock icon in the corner of our browser window… but very few people stop and think about exactly what that means, and what’s going on behind the scenes. So come along with me, and we’ll walk through what SSL means, and how it works.
First of all, SSL stands for Secure Socket Layer. This system was developed by Netscape in the mid-1990s for use with the Navigator web browser, the first to offer reliable e-commerce features. It addressed the problem that when browsing the web, anyone could spy on your communications. If some of those communications were a credit card number, or some other personal information, a criminal could do terrible things to you.
So what Netscape designed was a protocol – a way for two computers to talk with one another – that encrypted messages as they went from one computer to the other. This made it impossible for anyone except those two computers to read the message, so your secret information was safe.
What is a Certification Authority (CA)?
A Certification Authority (CA) is a trusted entity that issues digital certificates to verify the identity of individuals, organizations, or devices in a networked environment. It acts as a third-party intermediary that validates the authenticity and integrity of digital information, such as public keys and digital signatures.
The CA plays a crucial role in enabling secure communication over the internet by digitally signing certificates and vouching for the identity of the certificate holder. It ensures that the public key in a certificate belongs to the entity claimed and provides confidence in the trustworthiness of the certificate.
CAs follow specific security protocols and procedures to validate the identity of the certificate requester before issuing a digital certificate. They use cryptographic algorithms to create digital signatures and maintain a publicly accessible repository called a Certificate Revocation List (CRL) to revoke certificates if they are compromised or no longer valid.
Web browsers and other software applications trust the certificates issued by recognized CAs and use them to establish secure encrypted connections, authenticate websites, and verify the integrity of digital communications.
The way it works is for the owner of the web server to get what’s called a digital certificate from a company called a certification authority (CA). Each certificate comes with a link to the company that issued it, and eventually ends at what’s called a “root” CA.
Every browser has a list of CAs that are considered “trustworthy.” When you make a secure connection to a web server that has a digital certificate, your browser traces up what’s called the “chain of authority” – checking each certificate to see if the CA that issued it is in the list. If the browser gets all the way back to the root CA without finding it in the list, you get a warning that this certificate is not trusted.
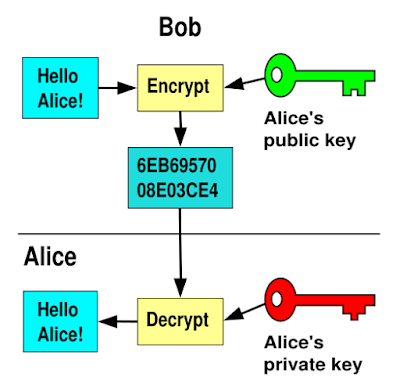 Public Key Exchange
Public Key Exchange
When a certificate is not trusted, you don’t know for sure that the information listed in the certificate – the company name, address, phone number, etc. – is accurate. Trusted CAs verify business licenses and contact information. Other CAs may not. But even if the contact information isn’t verified, the traffic between your browser and the web server is secure from eavesdroppers.
Once the browser has established that you want to trust this web site’s certificate, whether because the CA is in the browser’s list or you confirm your trust in the warning dialog, the two computers will exchange “keys.”
A “key” is just a large number that is mathematically related to another number in a very specific way. The way these numbers are chosen is complex; explanations of the process tend to start with things like “Agree on a finite cyclic group G with a generating element g in G.”
Like most cryptographic concepts, it’s probably easiest to just pretend it’s magic.
Each computer will create two keys. The special mathematical relationship of these keys guarantees that any data encrypted with one key can only be decrypted with the other. One of these keys is kept secret, and the second is sent to the other machine.
Once the keys are exchanged, each machine uses its own secret key and the key received from the other machine to encrypt any data it sends. When the other machine receives the data, it will decrypt the data using the two keys it has.
Because the keys will only decrypt data encrypted with the matching keys, each machine knows both that the message came from the same machine, and that it was intended for this machine. So the data is secure, and nobody can spy on it.
If you’re interested in making sure all your surfing is secure, then check out how you can use anonymous surfing software to protect your identity and connection.